Contents
In August, I attended the IEEE iThings 2022 conference to present a paper titled “IoT Droplocks: Wireless Fingerprint Theft Using Hacked Smart Padlocks”. If you have access to the IEEE Xplore library you can view the published version. I’ve made an arXiv preprint available as well. If you want a shorter, simpler version, read on below.
Still TL;DR
If all you want to see is videos and code, then I’ve made an open-access data publication of the following parts of this work:
What’s the deal?
Smart locks, at least some of them, have a fingerprint reader and some kind of wireless radio, like Bluetooth. They’re supposed to let you unlock them with an app or your fingerprint. They can be quite convenient, but are they safe?
I wanted to find out how easy it would be to turn one into something evil: a device that can steal the fingerprint of a victim by beaming an image of it wirelessly to someone nearby. I targeted smart padlocks, because they’re the most portable kind of smart lock. I call it a “droplock” because the idea is to leave it on the ground for a curious victim to find and pick up, a bit like when USB sticks containing malware are left for people to discover.
So, can you do it?
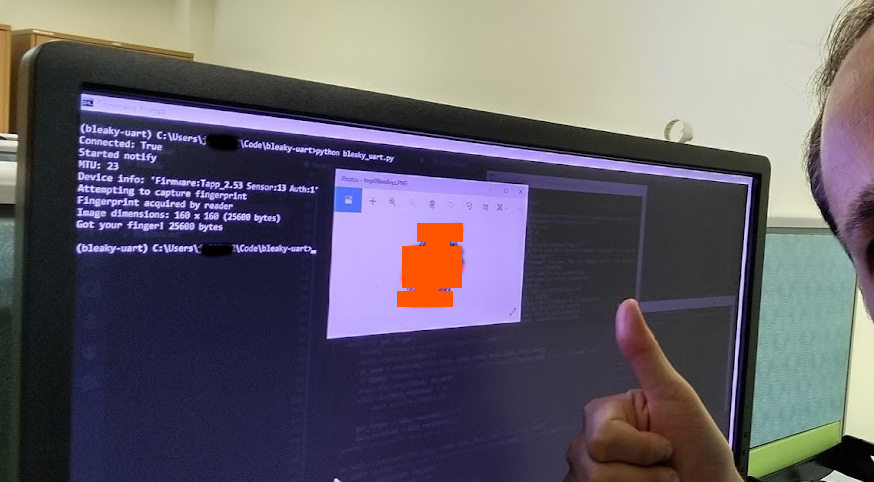
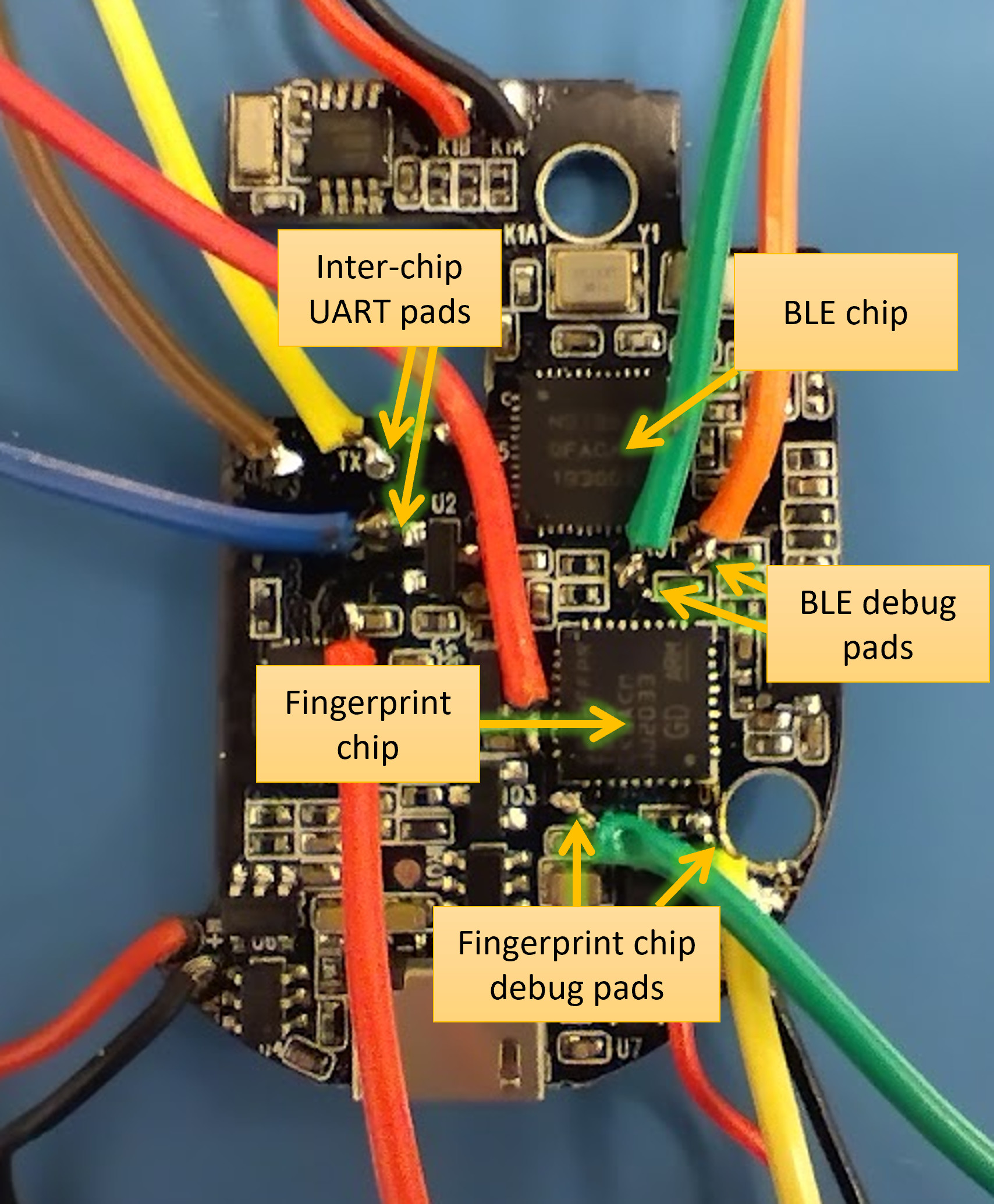
Yes I can! I made a proof of concept of the idea, but then I took a commercial lock and reprogrammed it with an evil firmware. If somebody picks it up and presses their finger onto the reader, it’ll send a copy over Bluetooth to a nearby receiver, and they might never know it happened.
Was it easy?
It was easier than it should have been, but it requires some embedded systems and reverse engineering skills to pull it off the first time around.
What can we do about it?
There are existing features and technologies that the device could have used to make the conversion harder, but they weren’t used. This kind of threat probably never crossed the mind of the designers or engineers. I also have some ideas for new ways to protect devices and people from these kinds of attacks.
Is it really a big deal, though?
Maybe, maybe not. We rely on fingerprints for a lot of security right now, so anything that puts that at risk should be given some attention. Somebody has to be motivated enough to create/convert these devices and leave them places that people will find and interact with them, all the while waiting nearby to receive data from them. After stealing a print, an attack using that print still has to be mounted against a target, which isn’t always simple, but it is possible.
What next?
I have made a few more discoveries in this area that I’m putting into a longer paper, so look out for that in the future. I also have some follow-on research that I’m working on with colleagues.
If you’re a device manufacturer, or somebody else with an interest in biometric security, I’d be very happy to talk to you about my work, both current and future.