The Virtual Private Network, or VPN, has become a familiar term amongst Internet users in recent years. Yet, the secure tunnelling technology has been around much longer. So, why is it popular now, why should this be considered harmful, and what do we do about it?
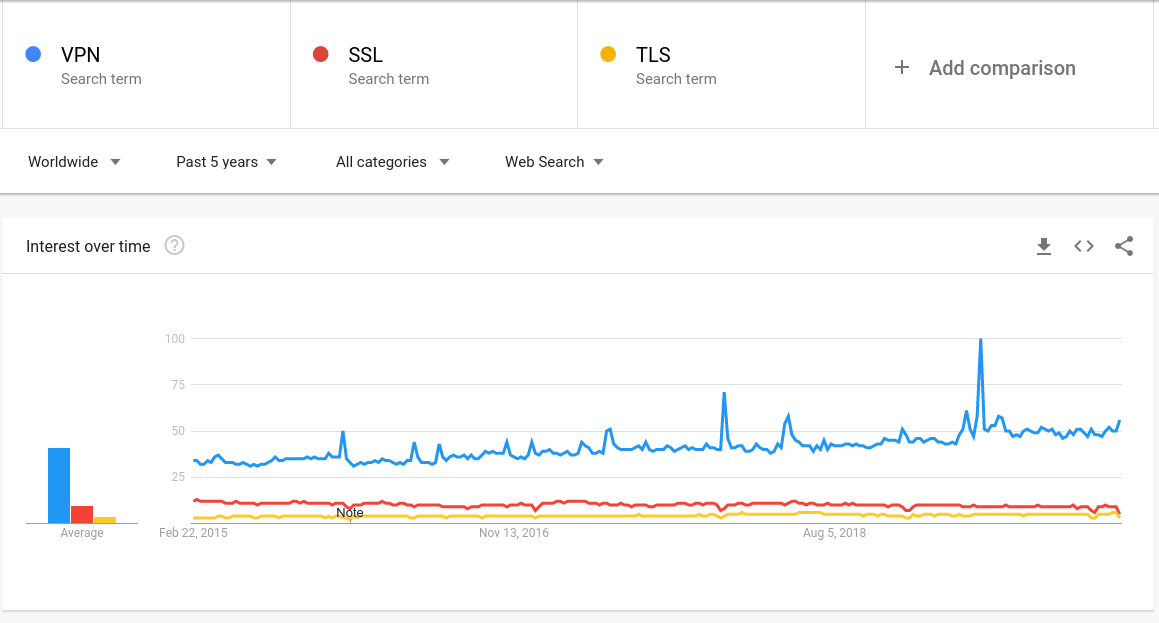
Take the global Google Trends for the terms VPN, SSL and TLS, pictured below. Comparatively few people seem to care about SSL and TLS, but VPN sees growing interest, with repeated spikes. But what does this mean for VPN?
This article explores the differences between personal and corporate VPNs, what needs the IoT ecosystem has for VPN, how personal VPNs may negatively affect the perception of VPN technology as a whole, and discusses what we can do to mitigate this image problem.
Problem: Not all VPNs are created equally
If we ask any random Internet user what a VPN is used for, there are two likely answers:
- “To disguise my traffic”
- “To login to my work resources from home”
If we dive deeper into these two perceived use cases, the crux of the problem emerges.
Personal VPN use
In recent years, VPNs for personal use have been promoted intensively online. The arguments for their use are many, but often include:
- Keep your data safe from snooping, especially in public WiFi areas
- Prevent ad companies and others from tracking you
- Watch streaming services that are not available in your country
- Bypass other provider- or government-imposed restrictions
Some of these uses are, at face value, a reasonable proposition. Others breach copyright, breach service agreements, or put you on the wrong side of the law, as this timely news from Kashmir demonstrates. But the general idea of a personal VPN is to encrypt your traffic between your device and some arbitrary second location on the Internet, to make your data safer, and make you harder to track. With people concerned about privacy, and frustrated by geo-fencing, it’s obvious why personal VPNs are growing in popularly. But here’s the problem with such services:
- How do you guarantee that the VPN provider isn’t tracking you?
- Even if they say they aren’t tracking you, what if they’re legally compelled to?
- If they have open source software to prove their approach is safe, how do you guarantee that’s what they’re running, and that’s how it’s configured?
- There are other threats to your privacy, such as browser fingerprinting, that a VPN cannot solve for you.
So now, the personal VPN is on shaky ground. But in the corporate world, and in the IoT ecosystem, we don’t talk about personal VPNs.
Corporate VPN use
Traditionally, a corporate VPN gives a remote site or user access to a company’s internal networks. The remote traffic is carried, encrypted, over the Internet, but tunnelled within is traffic that behaves as though the user is physically located at the target site. So, in a corporate scenario, VPN lets a user:
- Access a network remotely, as though they are a locally- or closely-connected part of that network.
- Trust that despite their physical location, the traffic between them and the other network is secure.
And just as importantly, as a company:
- Restrict who can remotely access a network
- Enforce policies for the strength of the security in the remote access
- Audit who connects and what they have access to
- Photo representing remote working / work from home
This puts corporate VPN almost completely at odds with personal VPN. While one seeks anonymity and access to all, the other seeks close tracking and tight access controls. Incidentally, corporate VPNs are likely being stressed right now, due to increased numbers of remote users in countries affected by COVID-19.
The danger
The risk here, is that personal VPNs make the term VPN a dirty word. If it becomes associated with “people hiding”, “dodging restrictions” and so on, it’ll immediately have negative connotations in the minds of decision makers. This makes life harder for the purveyors of VPN technologies, as well as the security teams that need to justify these technologies to decision makers.
What about IoT?
IoT’s role here is simple. Many IoT devices are remote, therefore many would benefit from VPN technology. If the use case of the device includes more than a single outbound application connection, then additional protection at the network-level becomes beneficial. Remember, even if you use strong TLS for your application sessions, defence in depth will lower your exposure to risk. I’ll cover VPN for IoT in more detail in a future article. For now, I’ll use a short example of where it fits into a defence in depth approach.
Take a remote IoT gateway that communicates with multiple services over a 4G or 5G network. Consider these layers:
- Protect the device from physical attack with Secure Element
- Protect the software/firmware with code signing
- Protect the wireless traffic with the best-available security technology for the connection in use, for example the algorithms available to 5G
- Protect the network traffic between the device and your datacenter with a VPN
- Protect the application connections with TLS
Having the fourth layer there means that the impact of any issues with item three or five are reduced somewhat. But, to justify investing in such measures, they must be efficient, in terms of cost, bandwidth and manageability.
At Microsec, we cater to exactly these issues, with a VPN technology that’s built around our LifeCycle Management System, that can integrate with your own IoT backends, dashboards, and device managers. So please, talk to us if you want to know more!
Fixing the image problem
Of course, we’d like to focus on justifying why our VPN solution is the right choice for your IoT needs. We’d prefer not to put time into explaining why VPNs aren’t nefarious veils of secrecy. Here are some suggestions from me:
- Be up-front about the distinction between corporate and personal VPNs
- Use the term “anonymous VPN” to refer to that particular sub-class of service
- Ensure the use-case of the product is easy to identify, for example “this is an IoT VPN product”
- Drop the term VPN from the lead-in entirely, and instead refer to it as “remote network encryption” or similar.
While many will already get the distinction, we need to ensure those that don’t can be given an explanation quickly and easily, to help them understand the benefits and relevance of appropriate VPN technologies.
Do you think this is a complete non-issue? Or do you think there’s a better way of dealing with this distinction? I look forward to hearing your thoughts!
Image credits
- Leaderboard photo by Mathew Schwartz on Unsplash
- Laptop photo by Anna Auza on Unsplash

About Microsec
Microsec is a Singapore-based company specialising in cyber security for IoT. We make it possible to secure and manage constrained devices running on IoT wireless network. We’re helping companies in Asia and around the world make secure solutions for smart nations, Industry 4.0 and digital transformation. Ask us about our Micro-PKI technology, Automated Certificate Management System, Micro Intrusion Detection System, or any of your IoT-/OT-focused security challenges.